LeftoverLocals: A Critical GPU Security Flaw in AMD, Apple, and Qualcomm Chips
This section will introduce the newly discovered security vulnerability called LeftoverLocals, affecting GPUs made by AMD, Apple, and Qualcomm. It will outline the potential risks posed by this flaw across various devices and operating systems.
Discovery of the Security Flaw by Trail of Bits
Focusing on the discovery, this part will detail the work of the researchers at Trail of Bits in uncovering the vulnerability. It will discuss the significance of their findings in the context of GPU security.
Also check Managing Network Connections with Windows Firewall
Impact of LeftoverLocals on Computing Devices
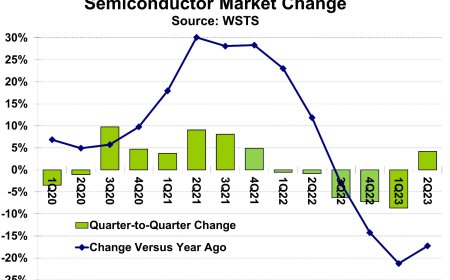
Here, the article will delve into how LeftoverLocals compromises the security of a wide range of computing devices, including smartphones, tablets, notebooks, PCs, and servers.
Mechanics of the LeftoverLocals Exploit
Analyzing the mechanics of the exploit, this section will explain how the vulnerability allows attackers to infiltrate other users' data via the GPU’s memory. It will describe the process of accessing and reading residual data left in GPU memory after execution.
Demonstration of the Vulnerability
Discussing the proof of concept presented by the researchers, this part will describe how they used the Llama.cpp program to demonstrate data access and theft using the exploit.
Testing and Identification of Affected GPUs
This section will detail the testing conducted by the researchers on 11 different GPUs. It will list the specific models found to be vulnerable, including the AMD Radeon RX 7900 XT and Apple’s GPUs in the iPhone 12 Pro and M2 MacBook Air.
Exclusions and Non-Affected Devices
Focusing on devices not affected by the flaw, this part will note the researchers' findings on GPUs that do not exhibit the vulnerability, such as those from Intel, Nvidia, Arm, and Imagination.
Reporting the Flaw to Authorities and Industry Bodies
Detailing the group’s responsible disclosure, this section will discuss how the research group reported the security risk to the US-CERT Coordination Center and the Khronos Group.
Acknowledgement and Response from GPU Vendors
Analyzing the responses from AMD, Apple, and Qualcomm, this part will cover how each company has acknowledged the issue and the steps they have taken or plan to take, including patches and firmware updates.
Apple’s Patch for Affected Processors
Focusing on Apple’s response, this section will discuss the patch released for the Apple A17 and M3 series processors and the lack of clarity regarding other impacted devices.
Qualcomm’s Firmware Update
This part will detail Qualcomm’s rollout of a new firmware update to address the vulnerability in some of its devices.
AMD’s Mitigation Plans and Timeline
Discussing AMD’s response, this section will describe the security bulletin they posted, the severity of the issue, and their mitigation plans, including the timeline for implementing a new mode to clear VRAM between processes.
Implications for GPU Security and User Protection
Analyzing the broader implications, this part will consider the impact of the LeftoverLocals vulnerability on GPU security and what it means for user protection across various devices.
Conclusion: Navigating GPU Security Challenges
Concluding the article, this section will summarize the challenges posed by the LeftoverLocals vulnerability and reflect on the ongoing efforts to enhance GPU security in the tech industry.
Additional Resources and Further Reading
Finally, suggestions for further reading and resources for those interested in learning more about GPU security, cybersecurity trends, and protective measures will be provided.