Hackers use malicious office documents as the latest trend in deceiving people
Placing malware within documents has been around for a long time, but it is still very successful in deceiving people and achieving the goal that the cybercriminals behind this type of attack want to achieve.

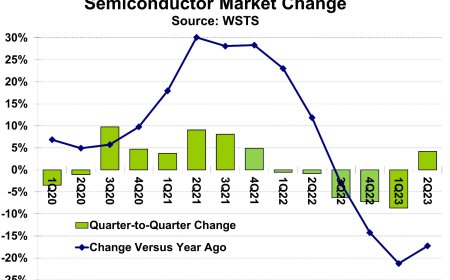
Their working principle is such that an “infected” document is sent to thousands and thousands of email addresses and then spreads further every time someone “stumbles” on a scam. Atlas VPN offered more detailed figures related to this type of attack, revealing that 43 percent of all malware downloads were related to malicious office documents.
The research was commissioned by Atlas VPN by Netskope Threat Lab and was conducted through July this year and concerns various office documents from all platforms, such as Microsoft Office 365, Google Docs, PDFs ...
Ultimately, the numbers themselves are worrying because, in the second quarter of last year, only 14 percent of malware was related to office documents. Then, in the third quarter of 2020, it “jumped” to 38 percent, which can be explained by the fact that the coronavirus pandemic took off, and thus there were many more potential victims.
Already in the third quarter, there was a drop to 34 percent and this was also to be expected as a habit of the pandemic was formed. The same percentage remained in the first quarter of this year, but with the second quarter, new growth was recorded.
It is EMOTET, one of the most dangerous malware spread in this way, through Word documents. And it was dangerous because it opened the "door" to other malware so that the victim would be affected from various sides and in various ways ...
And the solution to fighting this scourge is not to open unverified documents, use the ability to scan documents before opening them, and have the antimalware tools on your device. Thus, the level of prevention of “infection” that creates a whole range of problems can be significantly increased.
By: Amber V. - Zexron